Cyber Security: An International Security Issue with No Solution?
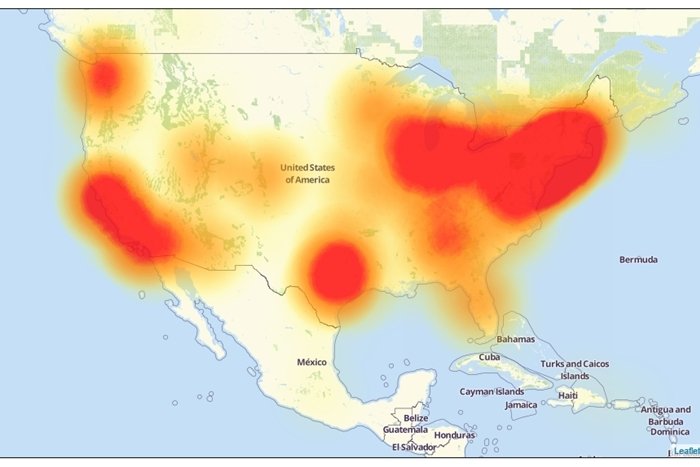
On Friday, October 20th, malicious cyber attacks prohibited access to major websites like Twitter, PayPal, and Amazon in intermittent locations throughout the U.S. and abroad. Experts determined the attacks are the result of a virus that infected thousands of users’ internet-connected devices through webcams and video recording devices. This method of hacking is both complicated … Read more